Access your home LAN securely via Internet from iPhone/iPad
Long story short, I am a heavy and very happy both iPhone/iPad and Mikrotik/RouterBoard home router user for about five years now and in this quick how-to I will show you how to create a PPTP VPN (VirtualPrivateNetwork) tunnel from anywhere on the Internet (3G or Wifi) from your iPhone/iPad to your home LAN using Mikrotik router. This is useful if you maybe want to access some files on your home computers, network drives or maybe want to remotely control your home PC with remote desktop from you iPad on 3G … what is really cool actually.
Contents
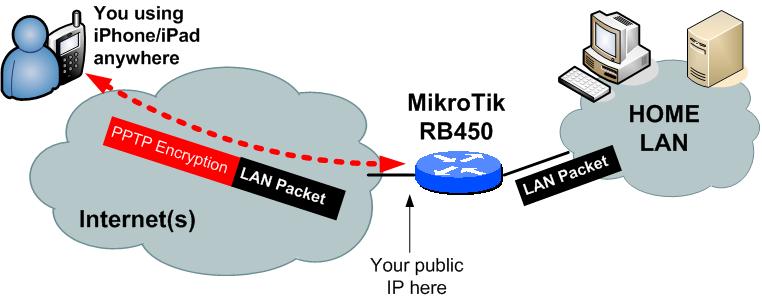
Logical topology:
This is a quick schema what we would like to have at the end. You can see iPhone at one end in the Internet with encrypted tunnel coming to your home network. Via the tunnel you can access all the home PCs or storage just as if being on your home WIFI.
Requirements:
- Mikrotik Router. I will use my RB450 router visible on the image below. I will show PPTP configuration for this router in this article, but generally with a little effort you might be able to translate the principles to other routers capable of doing PPTP server on your own. NOTE: You are not limited to this router selection, and if you have other PPTP enabled router, you can try to adopt this guide to that router.
- Public IP from your service provider – Yes, to have any device on the Internet be able to connect directly to your home router, your Internet Service Provider (ISP) has to provide you with a public IP address. You can use sites like whatismyip.com to find out your immediate IP address and then look on your PC/router if you have this IP yourself, or it is shared by multiple users by your ISP, what is not good and this whole setup will not work.
- iPad/iPhone. I will show configuration on iPhone/iPad but any PPTP device like, maybe Android based or even a PC with PPTP client can be connected the same way.
Mikrotik RB450:
This little beast that you can get for about $50 will be our router. It can do many things other than PPTP, but we will focus on PPTP only here.

Configuration – iPhone:
On iPhone, the configuration is very easy. You basically go to “Settings->VPN” and you will see empty VPN profile page as shown below:
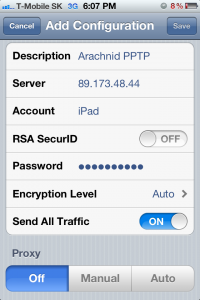
Cllick “Add VPN-Configuration” to your iPhone to create a new VPN profile. For this test, I will create one profile these test parameters:
VPN type: PPTP
Connection IP: 89.173.48.44 (or you can enter hostname like networkgeekstuff.com)
Account (username): iPad
RSA SecurID: off (this is used with certificates that we do not need for our purposes)
Password: <select your self one>
Encryption Level: Auto (the iPhone will try from the most strongest first then going to less secure for maximum compatibility)
Send all traffic: I will go with yes, this option instructs your iPhone if “everything” on your home LAN or only few networks. For example your iPhone will go to the internet via the VPN to your home first and then hopefully your home router will provide internet for him. For test purposes, you can go with YES as well.
Proxy: OFF – on this point we will not consider having HTTP proxy at home for internet access (although Mikrotik have one and is easy to create when needed later).
Below the parameters entered to iPhone directly:
Configuration – MikroTik:
Now the more interesting part. Lets create this access on the Mikrotik router. These examples already assume your normal internet access is working and you are not blocking incoming PPTP traffic coming from Internet (check if TCP 1723 and GRE traffic is not blocked).
Step 1 ) Lets start with creating a PPTP profile that will give both tunnel endpoints an IP address and enable encryption.
/ppp profile add name=iPadRemote local-address=195.168.4.14 \ remote-address=192.168.4.15 use-compression=yes use-encryption=yes
NOTE: The encryption is negotiated under PPP standard and is not super-strong by most today standards, but if you are not working with some very valuable data to be a target of any direct attack, this is enough for you. If you are security sensitive, you can have a look extending you VPN to IPSec/l2tp version that is also possible on Mikrotik, but is considerably harder to do.
Step 2) Then we create our “iPad” username with password and attached to the “iPadRemote” profile
/ppp secret add name=iPad service=pptp password=iPadRemotePassword \ profile=iPadRemote
Step 3) Now we configure the pptp-server on Mikrotik with the created profile and create virtual interface for the iPad username.
/interface pptp-server server set default-profile=iPadRemote \ authentication=mschap1,mschap2,chap enabled=yes /interface pptp-server add name=pptp-in-iPad user=iPad disabled=no
Starting your iPhone VPN to access home LAN file server
Now we have everything prepared, lets start the VPN on your iPhone. To do this, again go to “Settings->VPN” and click on the “OFF” button to start the VPN.
When you hit it, it will go via “connecting…” and “authenticating…” phases like seen below:
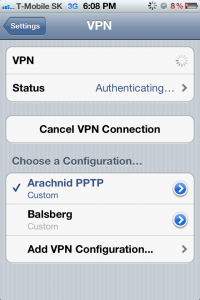
And voala! If your iPhone ends with “connected” and start counting connection time, this means you are connected on the VPN leading home.
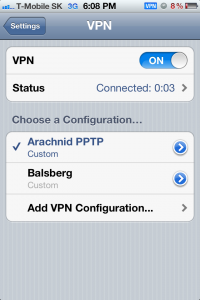
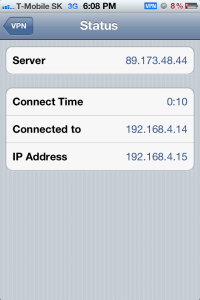
Verification
You can verify next by clicking the “Status” button and you will see some details. At minimum you should see the IP address configuration you received from via the PPTP tunnel. This is how it should look following this guide:
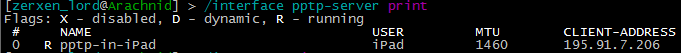
On Mikrotik when connected you can have a look if the pptp virtual interface is up in both the /interface pptp-serve print and also routing table with /ip route print. Examples below:
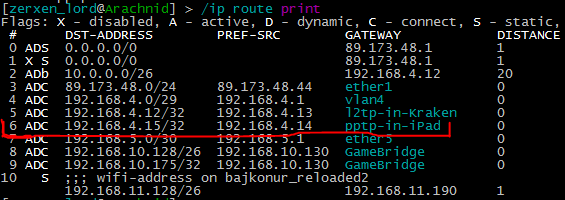
The other thing you can now test is anything that usually only work from your local LAN network. It can be accessing some of your home file servers, remote desktop or playing LAN games with someone. Also possible with this setup is to sometimes avoid any web filters if you are in hotel or airport. You can setup for yourself a HTTP proxy at home and point your VPN configuration to this proxy. This way if at minimum the VPN works, you will always have the unfiltered home internet.
Summary
In summary you have just connected your home LAN with iPhone. The usefulness of this is easily visible by many of you. And I encourage you to play with it or maybe extend this solution few steps further with HTTP proxy.




One comment ...
Comments are closed.